- Visually engaging animated explainers simplifying complex information-security risks
- Short, narrated micro-modules designed for high retention
- Real-world cyberattack and breach scenarios
- Embedded knowledge checks throughout the course with scores
- Structured final assessment
Learning Objectives
By the end of Information Security Awareness eLearning Training, learners will be able to:
- Know the significance of employee’s role in securing organizational IT infrastructure.
- Recognize common types of IT security breaches.
- Understand the strategies to mitigate attacks such as phishing, malware, and hacking.
- Maximize the safety of personal and corporate IT resources.
- Classify data based on sensitivity for enhanced protection.
- Understand safe utilization of AI and safeguarding against AI-based attacks.
Why Information Security Awareness eLearning Training?
Reduces human-led Cyber Risk across the organisation
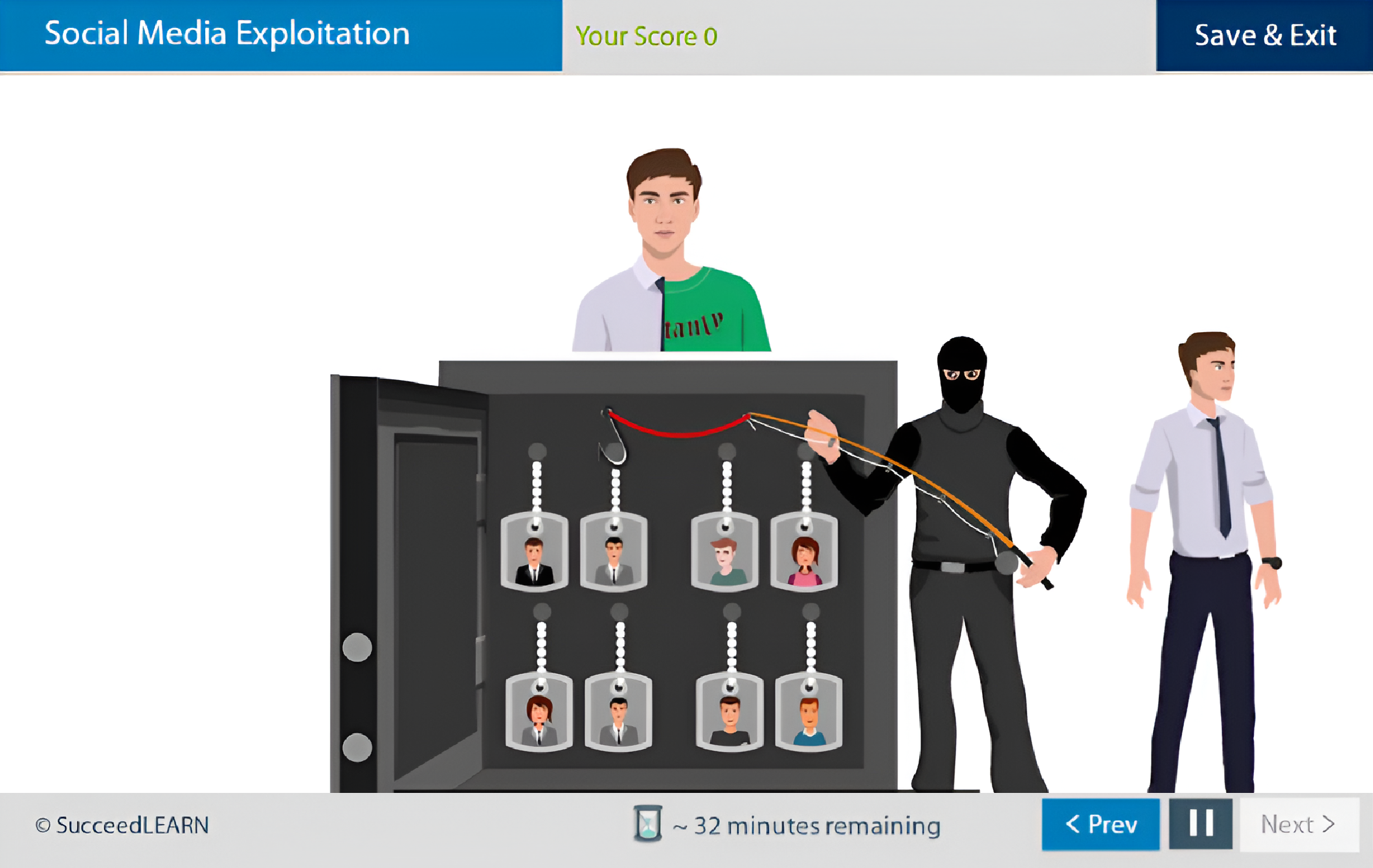
The training explicitly positions employees as a potential “weak link” in information security and equips them with practical, scenario-based guidance to prevent phishing, social engineering, malware, ransomware, and attacks through social media thereby addressing the most common root cause of breaches, that is, human error.
Improves compliance with internal policies and regulatory expectations
Unclear classification makes it easier for attackers to identify valuable data and exploit it for malicious purposes. By training employees on information classification (Public, Internal, Confidential, Restricted, Legal) and secure handling practices, the course helps organisations demonstrate due diligence, data-protection accountability, and policy adherence expected by regulators, auditors, and clients.
Minimises financial loss from Phishing and Fraud Incidents
Realistic scenarios including email phishing, smishing, vishing, safe internet browsing and safe banking practices, teach employees how to verify communications before acting, reducing the likelihood of credential theft, fraudulent payments, and ransomware payouts.
Enhances account and access security across the enterprise
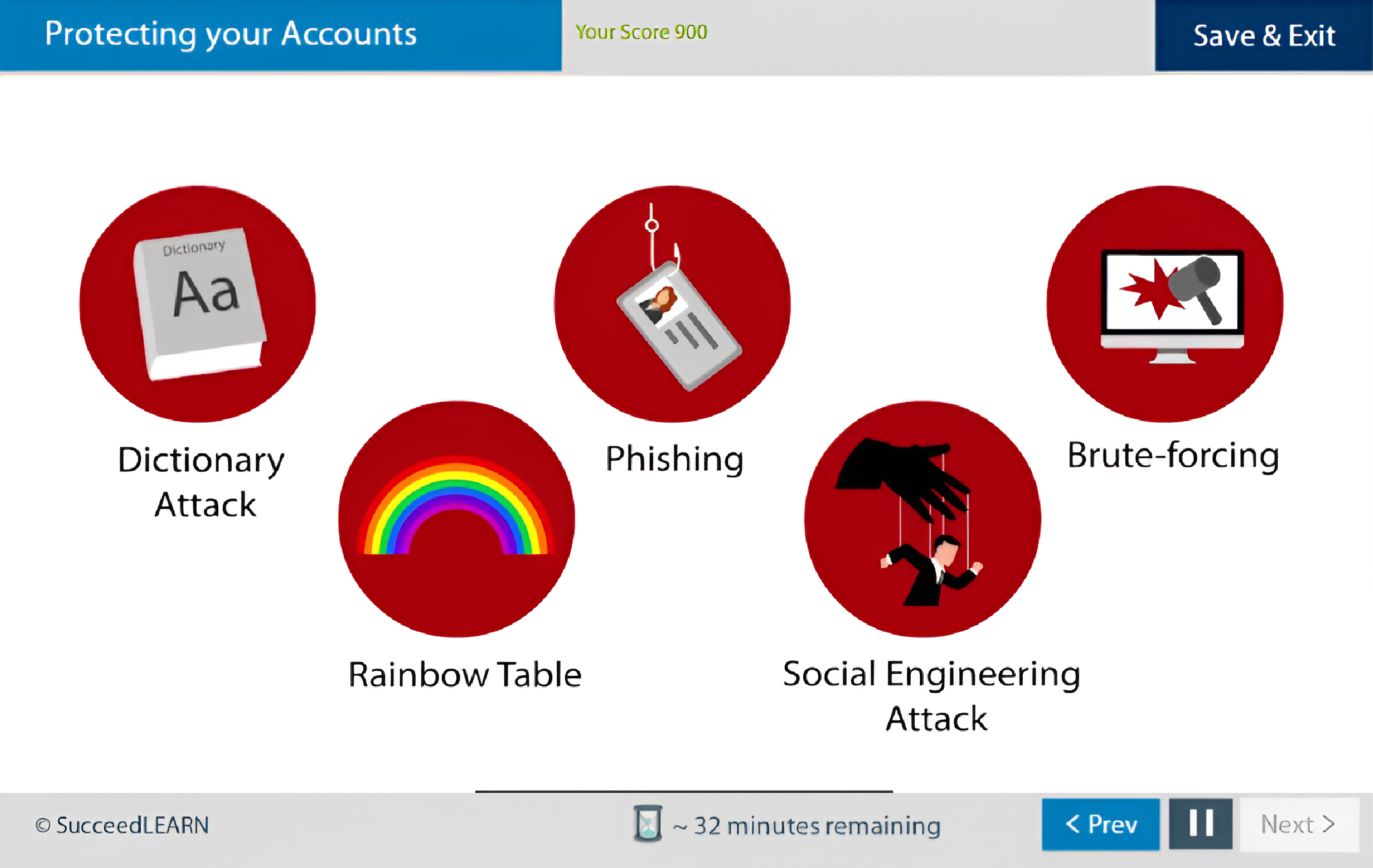
The training reinforces strong password creation, 2 factor authentication and MFA (Multi-Factor Authentication) usage, controls that are essential to preventing unauthorised access to corporate systems, cloud platforms, and internal networks.
Safeguards Physical and Digital Assets
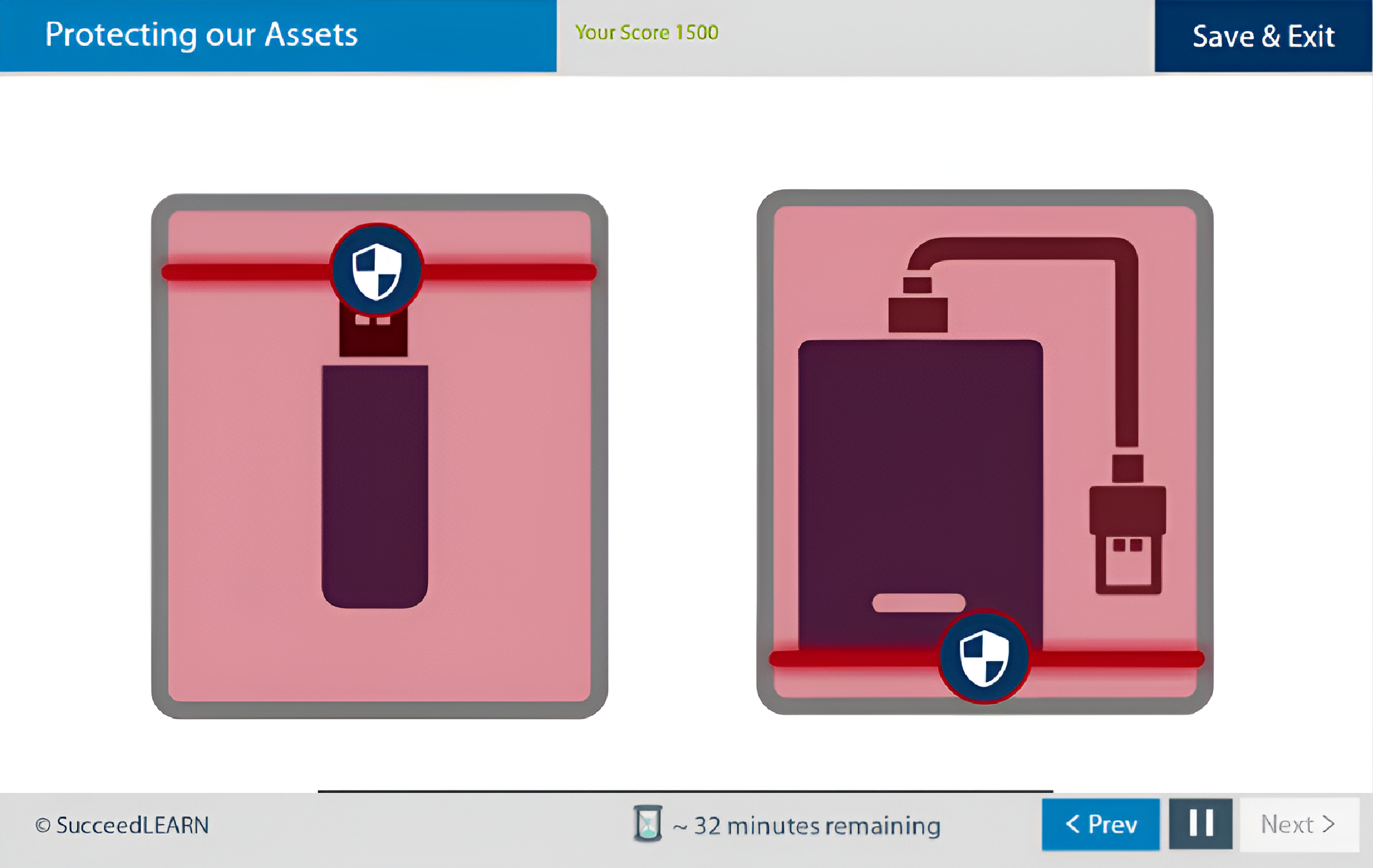
Employees are trained on secure handling of devices, USB drives, laptops, phones, visitor management, and physical access controls thereby reducing the risk of data exposure through lost devices, unattended systems, or unauthorised physical access.
Innovative Assessment tasks
As each micro-module is explained, the knowledge of learners is immediately checked through innovative scenarios and a score given that adds up to the final assessment score making the training practical and engaging thus reinforcing retention.
Course Structure
Learning elements
Format & accessibility
Fully responsive interface across desktop, tablet, and mobile -complete with a learner dashboard, progress tracking, automated reminder prompts, and seamless integration with your existing LMS or HR systems.
Certificate
On successful completion and passing the assessment, learners can generate a completion certificate as proof of training (configurable per org).
Target Audience
The course is tailored for:
- All employees handling organisational IT systems, data, or digital tools
- Staff exposed to email, messaging platforms, social media, and remote-working environments
- Employees with access to confidential, restricted, or intellectual property data
- Managers and senior leaders vulnerable to targeted attacks such as whaling and impersonation
- Remote and hybrid workers accessing corporate systems from home or public networks
Real-World Cybersecurity Incidents & Regulatory Consequences
Laws and standards such as GDPR, ISO 27001, and sectoral cybersecurity regulations require organisations under sectors such as Financial Services & FinTech, Healthcare & Life Sciences, E-commerce & Retail, Manufacturing & Industrial Organizations, etc, to implement “appropriate technical and organisational measures.” Training employees to recognise phishing, social engineering, malware, data-handling risks, and remote-work threats is a key organisational control expected by regulators.
Below are a few cases where companies faced severe penalties and scrutiny for failing on compliance measures:
- British Airways (2018)
A phishing-enabled compromise led to the theft of customer payment data affecting over 400,000 customers. The UK ICO imposed a £20 million GDPR fine, citing insufficient security controls and employee awareness failures in protecting credentials and systems. - Colonial Pipeline (2021)
A single compromised password (no MFA) enabled a ransomware attack that shut down fuel supply across the U.S. East Coast. The company paid USD 4.4 million in ransom and faced intense regulatory and public scrutiny, highlighting failures in account security training.
Course Outline
Common Security Topics
Social Media Exploitation
Phishing
- SMS frauds – Smishing
- Vishing
- Safe Internet Browsing
- Safe Banking Practices
Protecting Your Accounts
Malware
Protecting Your Assets
- USB Pen Drive/Secondary Storage
- Mobile Phones
- Physical Security
Information Classification & Handling
- Public Data
- Internal Data
- Confidential Data
- Restricted Data
- Legal Records
Total Duration: 75 Mins
FAQs
Employees are a primary target for cybercriminals. The training equips staff to recognise and prevent phishing, social engineering, malware, ransomware, attacks through social media, and data-handling risks thereby reducing the likelihood of breaches caused by human error.
Yes. The course provides detailed coverage of phishing variants including email phishing, smishing, vishing, and spear phishing supported by realistic scenarios that teach employees how to verify communications before acting.
Employees are trained on information classification (Public, Internal, Confidential, Restricted, and Legal), secure data handling, and reporting data loss supporting organisational privacy, confidentiality, and regulatory obligations.
The course covers strong password creation, 2 factor authentication, multi-factor authentication (MFA), stressing on the ways these could be used to reduce the risk of avoidable security threats, thereby helping prevent unauthorised access to corporate systems and cloud platforms.
The course includes guidance on protecting laptops, USB drives, mobile devices, visitor management, and secure workspace practices thereby reducing risks from lost devices, unauthorised access, and physical data exposure.
Embedded knowledge checks, interactive activities, and a final assessment provide measurable evidence of employee awareness thereby supporting audits, investigations, client security reviews, and cyber-insurance requirements.
The training is relevant for all employees, with particular importance for staff handling data, IT systems, remote access, collaboration tools, confidential information, and senior leaders who may be targeted by impersonation and whaling attacks.
The delivery is fully flexible. If you have an in-house LMS, we can provide the course as a SCORM-compliant package. If not, we offer a seamless SaaS-based hosting option for easy access and deployment.