- Visually engaging animated explainers
- Concise, narrated micro-slides
- Real-world case examples
- Frequent knowledge checks and quizzes
- Final assessment
Learning Objectives
By the end of this course, learners will be able to:
Social Engineering:
- Identify and assess social engineering threats across multiple channels
- Apply correct response and reporting actions in real-world scenarios
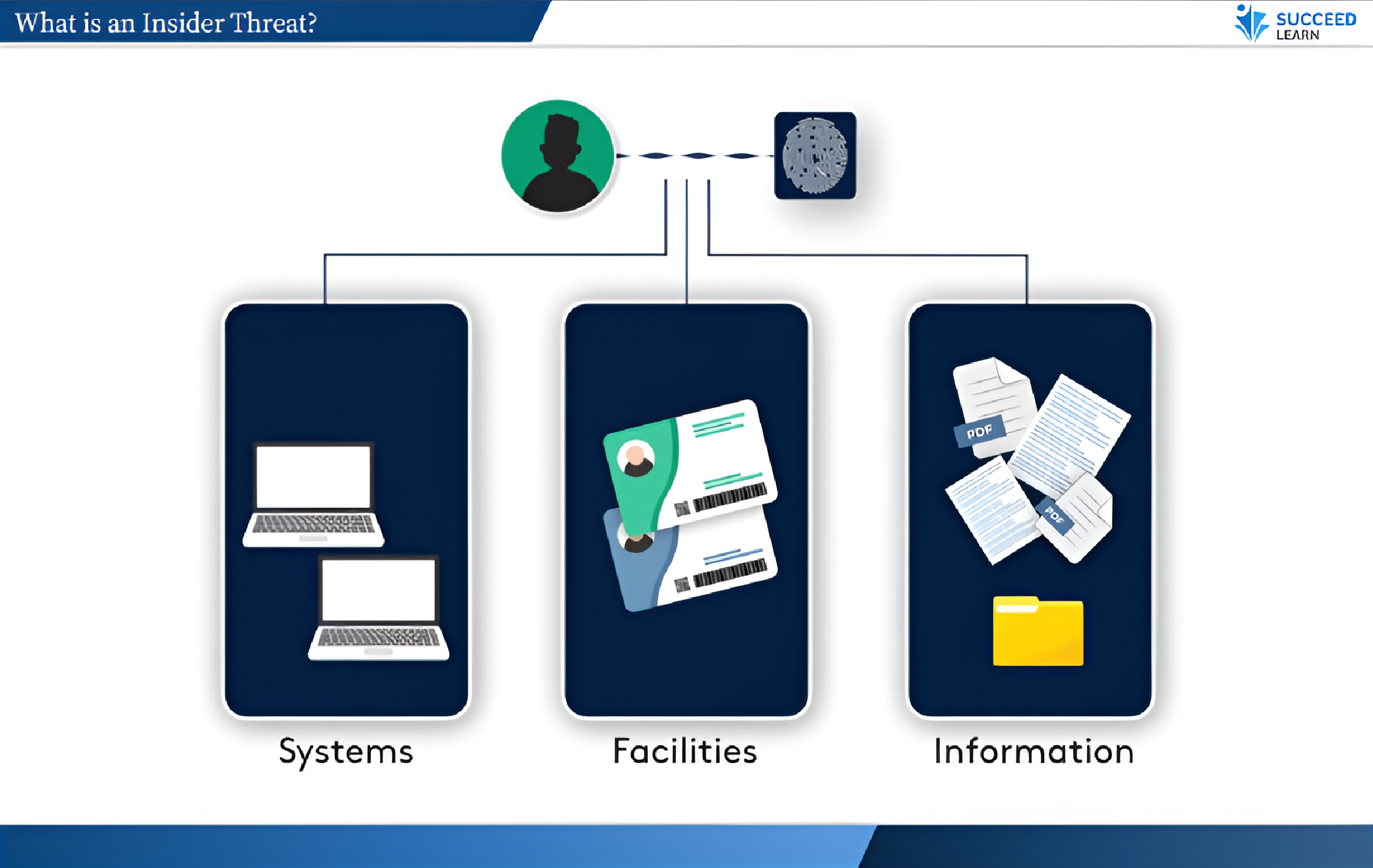
Insider Threat:
- Identify insider threat types and high-risk behaviours - including malicious, negligent, and compromised actions
- Apply correct prevention and reporting actions
Physical Security:
- Identify and apply core physical security practices
- Respond appropriately to physical security incidents
Data Privacy Training:
- Tell Personal Data from Special Category Data
- Understand and apply lawful bases for processing personal data
- Handle data safely through its lifecycle
- Recognize and respond appropriately to data-subject rights requests and DSARs
- Identify, assess, and report data protection incidents
- Manage third-party data sharing and cross-border data transfers responsibly
- Identify AI privacy risks
Third Party Risk:
- Identify and manage third-party risks
- Apply secure data-sharing practices with third parties
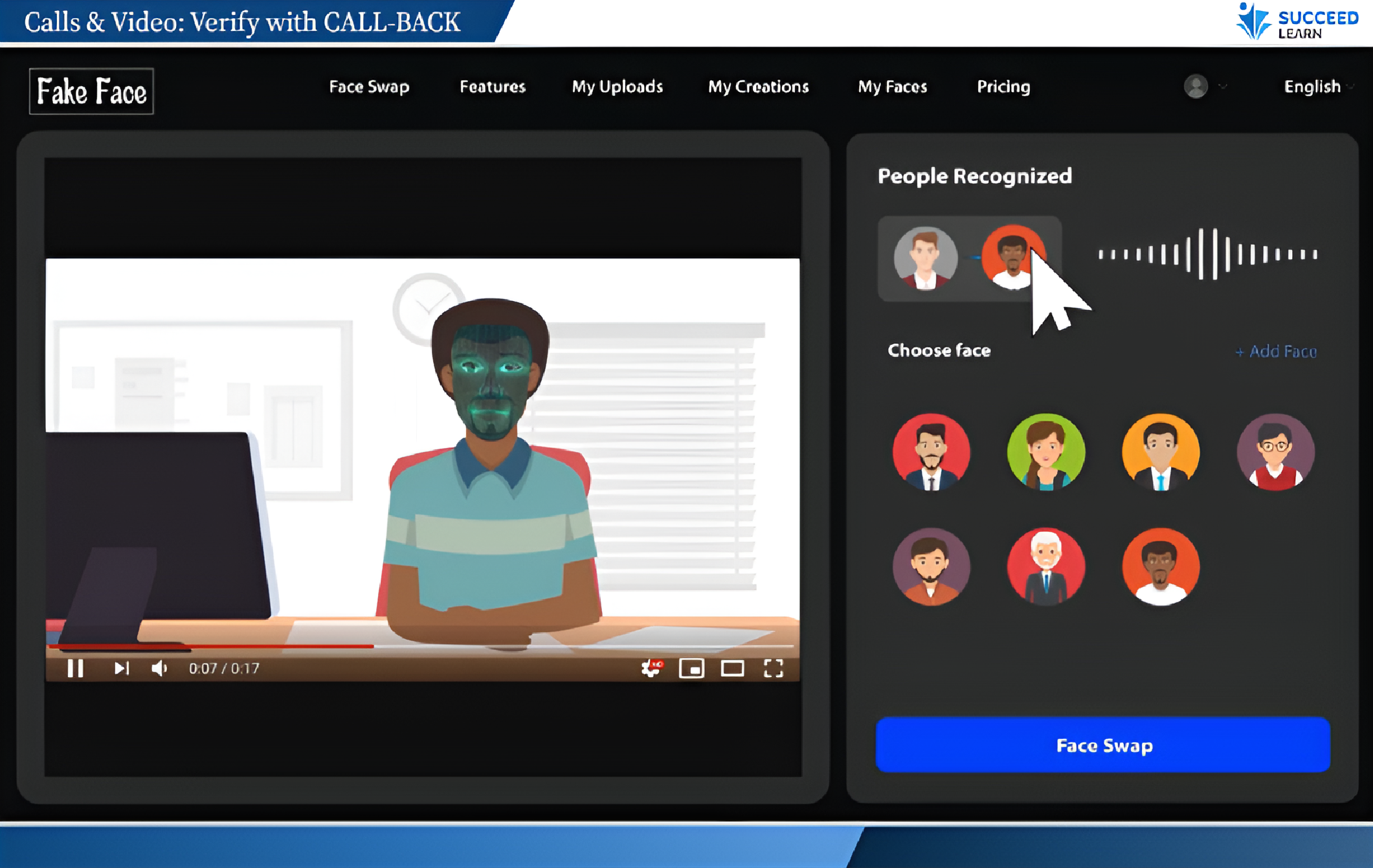
AI Based Attacks:
- Recognise AI-driven threats
- Apply practical verification and escalation steps
Why Security Awareness Training for BFSI and PE/VC?
Reduces the risk of high-impact cyber incidents and financial loss
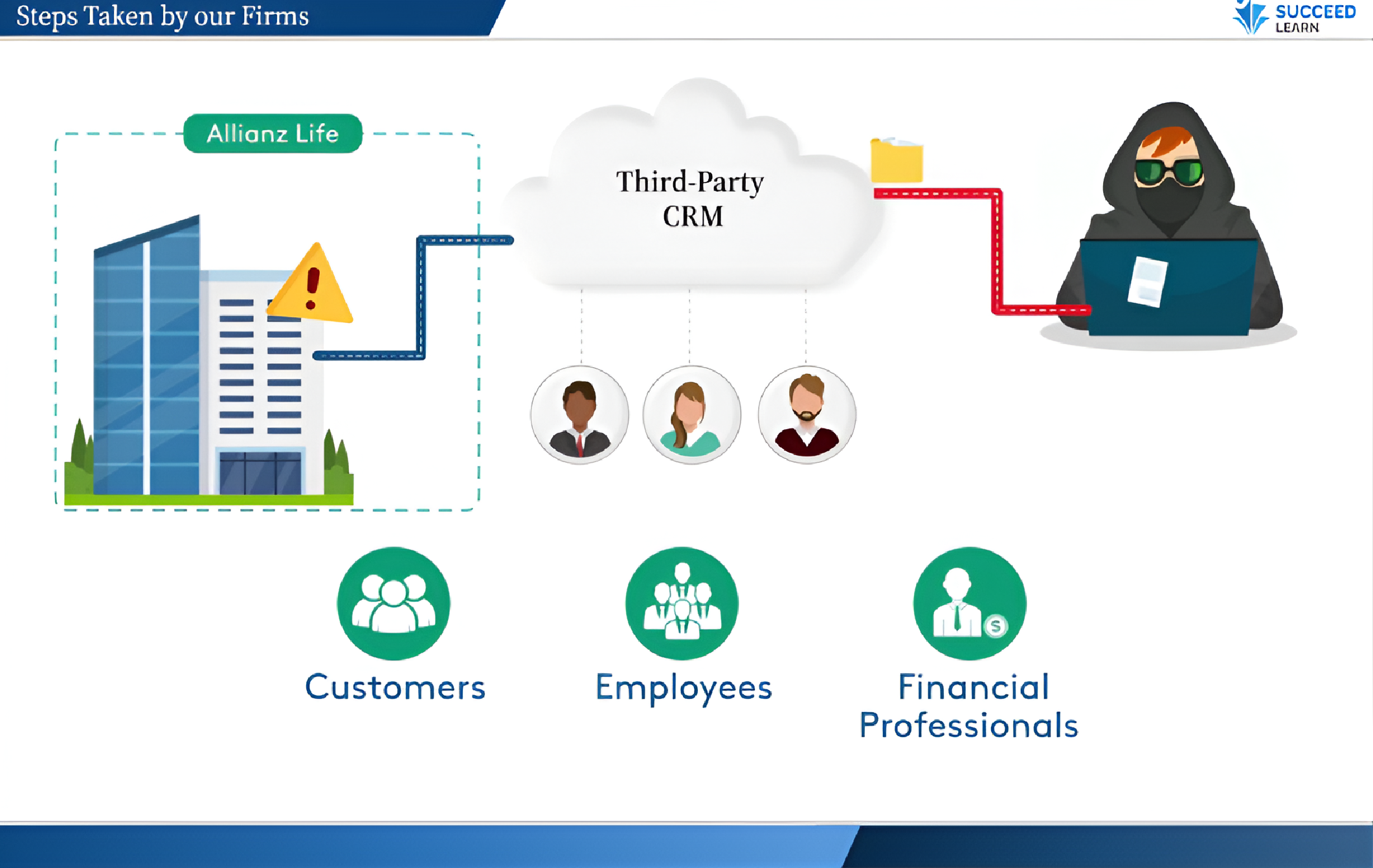
The training directly addresses real-world social-engineering threats, as illustrated by the January 2025 ransomware and data-exfiltration incident at a leading PE/VC firm, demonstrating how human error can bypass even advanced technical controls and expose sensitive financial, employee, and investor data.
Improves incident response speed and limits organisational damage
By training employees to recognise phishing, vishing, smishing, and deepfake-enabled attacks and to follow clear “STOP | REPORT | RETAIN” procedures, the Social Engineering Training enables faster reporting, quicker containment, and limiting how far and how severely an incident spreads once a security lapse occurs.
Safeguards the organisation from severe, hard-to-detect insider threats
By training employees to recognise malicious, negligent, and compromised insider behaviours, the Insider Threat Training directly mitigates risks that can lead to investigations, penalties, and loss of investor and client trust, particularly relevant given that insider threats account for a significant share of reported breaches.
Prevents physical security lapses that trigger data breaches and regulatory fallout
The Physical Security training directly addresses common physical security failure points, such as tailgating, unsecured devices, forged badges, and unattended confidential information, that can rapidly escalate into data breaches, regulatory notifications, and reputational damage, as demonstrated by the real-world case of a lost unencrypted laptop leading to reporting and transaction delays.
Reduces data privacy enforcement risk through timely, correct employee action
The training directly addresses common enforcement triggers such as delayed breach notification, mishandled DSARs, excessive data retention, and unsafe third-party sharing through scenario-based guidance and clear escalation protocols, helping employers demonstrate “appropriate organisational measures” and avoid penalties.
Strengthens consistent application of third-party risk controls across the organisation
By clearly defining employee responsibilities around vendor approval, data sharing, onboarding, and contract review, the training ensures that established safeguards (DPIAs, security questionnaires, audit rights, and approved platforms) are applied correctly in day-to-day operations, reducing the likelihood of policy breaches that could escalate into firm-wide incidents.
To mitigate escalating financial fraud and operational risk
The AI Based Attacks Training equips employees to recognise and verify AI-driven deepfakes, phishing, and impersonation attempts, which have already resulted in multi-million-dollar losses for organisations due to unauthorised payments and fraudulent instructions.
Laws & Regulations Addressed in Security Awareness training for BFSI and PE/VC
| Legislation / Concept | Relevance in the Course |
|---|---|
| General Data Protection Regulation (GDPR) | The Data Privacy Training is designed to operationalise GDPR requirements by training employees on lawful basis, personal and special-category data handling, data minimisation, retention, DSAR routing, breach identification and 72-hour reporting, third-party sharing, cross-border transfers, and accountability, helping employers demonstrate compliance through workforce awareness and defensible controls. |
| EU Digital Operational Resilience Act (DORA) | Establishes direct accountability for organisations, particularly financial entities, for ICT (Information and Communication Technology) and security risks arising from third-party service providers, making employee awareness of vendor onboarding, data sharing, and ongoing oversight a regulatory necessity addressed by this training. |
Course Structure
Learning elements
Format & accessibility
Fully responsive interface across desktop, tablet, and mobile -complete with a learner dashboard, progress tracking, automated reminder prompts, and seamless integration with your existing LMS or HR systems.
Certificate
On successful completion and passing the assessment, learners can generate a completion certificate as proof of training (configurable per org).
Target Audience
- All employees and contractors with access to organisational systems, data, or physical premises
- Customer-facing, finance, HR, legal, and operations teams exposed to fraud, data misuse, and impersonation risks
- IT, information security, privacy, and compliance teams responsible for safeguarding systems, data, and controls
- Managers and people leaders overseeing access rights, data handling, and employee conduct and receiving voice, video, or digital instructions from senior leadership, clients, or external stakeholders requiring verification.
- Senior leaders, executives, and executive assistants who are frequent targets of sophisticated attacks
- Employees handling personal, sensitive, confidential, or regulated information in digital or physical form
- Facilities, administration, and security staff managing building access, visitor controls, and asset protection
- Remote, hybrid, and mobile workers handling devices, documents, and communications outside secure offices
- Employees who engage with external vendors, service providers, or cloud platforms
- Employees handling payments, sensitive data, or market-sensitive information.
Case Studies: Real Consequences of Non-Compliance
Although Social Engineering, Insider Threat, Physical Security, Data Privacy, Third-Party Risk, and AI-based Attacks training are not always explicitly mandated as standalone legal requirements, regulators consistently expect documented, role-based security and privacy training as part of reasonable organizational controls. Companies that fail to train employees on threat recognition, data handling, vendor risks, and incident reporting face significantly higher penalties after incidents, making such training effectively mandatory in practice to demonstrate compliance, due diligence, and risk reduction.
Following are a few cases of companies facing penalties, thus highlighting the need for compliance:
- Interserve Group Limited (UK) was fined £4.4 million by the UK Information Commissioner’s Office (ICO) after a phishing email enabled attackers to access internal systems and compromise the personal data of over 100,000 employees. The regulator concluded that the breach stemmed from a social-engineering attack combined with inadequate security awareness and response controls, highlighting the compliance risk of insufficient employee training.
- Morgan Stanley – Insider Data Misuse (United States)
In 2016, Morgan Stanley faced regulatory action after a former financial advisor misused authorised system access to extract data relating to approximately 350,000 client accounts and attempted to transfer it externally. The incident resulted in enforcement scrutiny, litigation exposure, reputational damage, and a significant compliance remediation programme, highlighting how failure to adequately prevent, monitor, and train employees on insider threat risks can lead to severe regulatory and business consequences. - Target Corporation (2013): A major data breach occurred after attackers accessed Target’s network through a compromised third-party vendor, exposing millions of customer records. Target paid USD 18.5 million in regulatory settlements with U.S. states and incurred substantial remediation and legal costs, highlighting how weak third-party oversight and lack of employee awareness can lead to severe financial and reputational consequences.
Course Outline
FAQs
BFSI stands for Banking, Financial Services, and Insurance. It refers to the industry sector that provides financial products and services, including banks, investment firms, lending institutions, insurance companies, and other financial organizations. The BFSI sector handles sensitive financial and customer data and is highly regulated to ensure security, compliance, and consumer protection.
PE/VC stands for Private Equity and Venture Capital. It refers to investment firms that provide capital to private companies. Private Equity (PE) typically invests in established businesses to improve performance and drive growth, while Venture Capital (VC) focuses on funding early-stage startups with high growth potential.
BFSI (Banking, Financial Services, and Insurance) and PE/VC (Private Equity / Venture Capital) organisations handle high-value financial transactions, confidential investor data, and market-sensitive deal information, making them prime targets for cybercriminals. A single phishing email, fraudulent payment request, or compromised account can result in significant financial losses, regulatory penalties, and reputational damage. Because these sectors operate under strict regulatory oversight and high levels of client trust, security awareness training is essential to reduce human error, strengthen fraud prevention, protect sensitive data, and demonstrate strong governance and risk management practices.
Because social-engineering attacks deliberately target employees rather than systems, a single human action can bypass MFA, email filtering, and monitoring tools. This training strengthens the human layer of defence, which regulators and insurers increasingly view as a baseline control.
The course helps reduce the risk of data breaches, ransomware incidents, wire fraud, unauthorised payments, and credential compromise - events that can trigger regulatory penalties, financial loss, operational disruption, and reputational damage.
Yes. The course is scenario-driven and covers realistic phishing, vishing, smishing, and impersonation attacks across email, phone, messaging apps, and video calls, enabling employees to practice correct decision-making in high-risk situations.
Employees are trained on clear “STOP | REPORT | RETAIN” procedures, ensuring suspicious activity is reported immediately. Early reporting reduces the blast radius of incidents and enables security teams to contain threats before they escalate.
Insider threats pose a significant risk because employees, contractors, or partners already have legitimate access to sensitive systems and data. The training helps employers reduce the likelihood of internal misuse that can trigger regulatory scrutiny, financial losses, and reputational damage.
The course covers malicious, negligent, and compromised insider threats thereby ensuring employees understand both intentional misconduct and accidental actions that can lead to data breaches or security incidents.
By enabling early identification of warning signs and encouraging prompt reporting to the IT team, the training helps organisations contain incidents quickly, preserve evidence, and limit operational disruption and remediation costs.
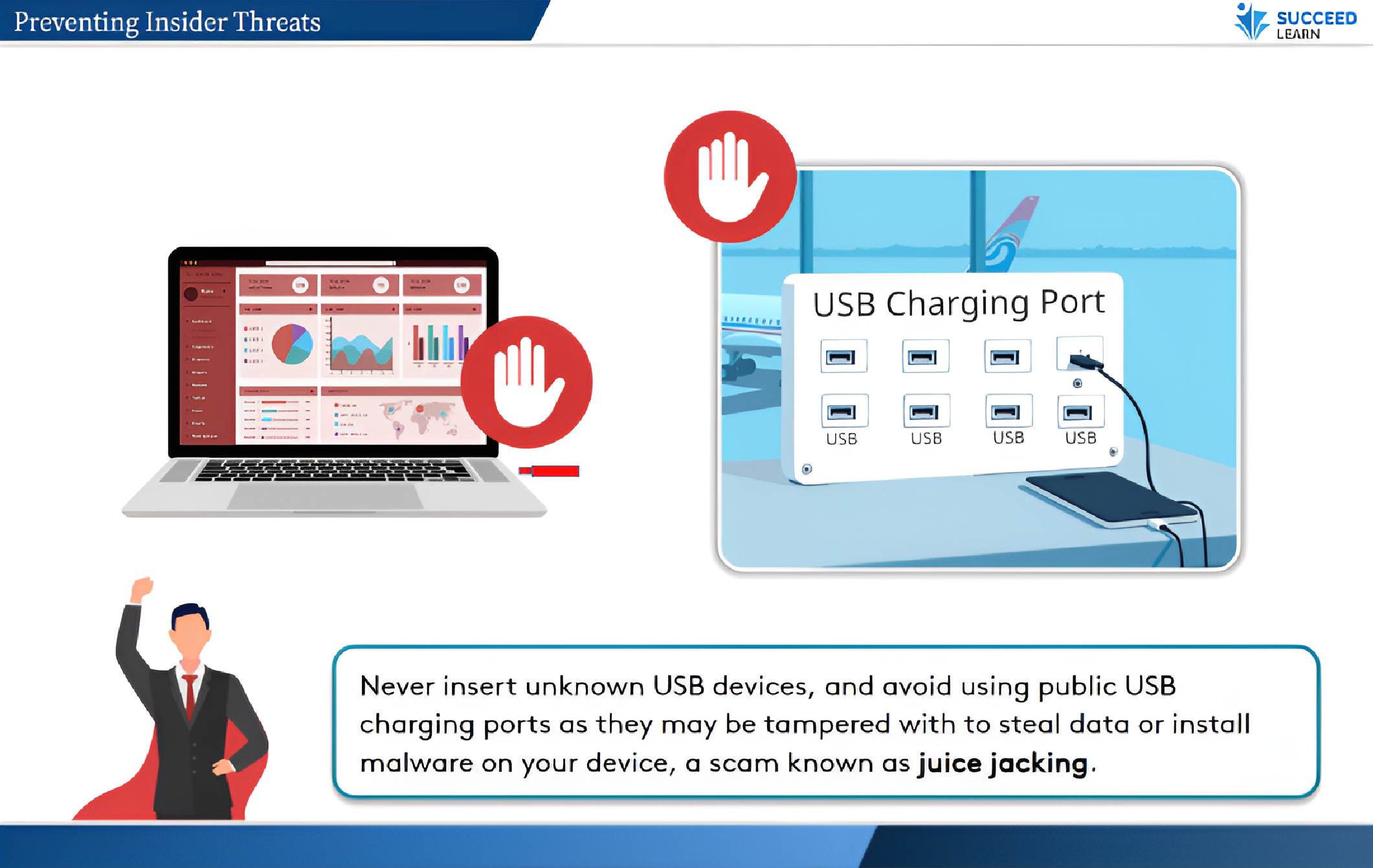
Yes. The course explicitly focuses on negligent insider behaviour such as misdirected emails, unsecured devices, or use of unapproved tools which are common causes of internal data exposure and regulatory findings.
Physical security failures such as tailgating, unsecured devices, or improper visitor access can directly lead to data breaches, regulatory exposure, and reputational damage. This training addresses everyday behaviours that often cause incidents and helps employers reduce both cyber and physical risk.
Yes. The course reinforces mandatory organisational safeguards including access badge controls, visitor escorting, clear desk and locked screen practices, secure device handling, and incident reporting, helping employers demonstrate policy adherence and due diligence.
Employees become the first line of defence by challenging unauthorised access, securing workspaces and devices, and promptly reporting loss, theft, or suspicious activity, enabling faster containment and reduced impact for the organisation.
The course builds documented awareness around lawful basis, data minimisation, retention, DSAR handling, incident escalation, and third-party governance thereby providing auditable evidence that the organisation has proactively trained staff on core GDPR principles.
Yes. The training explicitly addresses common breach scenarios such as misdirected emails, improper data sharing, duplicate storage, and delayed reporting, reinforcing correct behaviour through scenario-based decision making and clear escalation paths.
Employees are trained to recognise personal data breaches beyond cyberattacks, act immediately to contain incidents, and escalate without delay thereby supporting the organisation’s ability to assess and meet the GDPR 72-hour notification requirement where applicable.
The course ensures employees can recognise potential data subject rights requests and route them through the formal intake process, reducing the risk of missed deadlines, inconsistent responses, or unauthorised disclosures.
Yes. It reinforces vendor due diligence, contractual safeguards, approved transfer mechanisms, and the requirement to avoid unapproved tools thereby helping employers control downstream processing risks and regulator scrutiny.
By combining lifecycle controls, classification, minimisation, retention rules, and responsible AI practices, the training integrates privacy-by-design into everyday decision-making rather than treating compliance as a one-time exercise.
Yes. Completion records, assessments, and consistent employee guidance provide strong supporting evidence that the organisation has taken reasonable and proportionate steps to educate staff and prevent privacy violations.
Third-party breaches can expose our systems and Confidential or Highly Confidential data even when internal controls are strong. This training helps reduce regulatory, financial, and reputational risk by ensuring employees follow approved vendor and data-sharing processes.
Yes. The training reinforces employee responsibilities under regulatory expectations such as DORA, where organisations are directly accountable for ICT (Information and Communications Technology) risks arising from service providers, and supports audit readiness for listed entities.
While the firm maintains formal controls (vendor inventories, DPIAs (Data Protection Impact Assessment), contracts, audit rights), employees play a critical role by using only approved vendors, requesting reviews before sharing data, and escalating risks promptly.
It helps prevent unauthorised data sharing, use of unapproved vendors, weak contractual safeguards, and delayed risk reporting that are common causes of third-party breaches that can escalate into firm-wide incidents.
By ensuring employees consistently follow documented third-party risk controls, the organisation can demonstrate reasonable steps, due diligence, and policy adherence during regulatory reviews or breach investigations.
Non-compliance may lead to internal disciplinary action, regulatory scrutiny, breach investigations, and significant reputational damage if a third-party incident becomes an organisational breach.
AI-driven deepfakes, voice cloning, and phishing attacks have increased sharply and are already causing significant financial losses and reputational damage to organisations. This training helps employees recognise and stop such attacks before harm occurs.
The course helps reduce the risk of unauthorised payments, payroll diversion, data leakage, and market manipulation, while also limiting regulatory scrutiny and loss of stakeholder trust following a fraud incident.
Yes. The course highlights that AI-based attacks primarily exploit human trust and urgency. Employee awareness remains a critical control layer alongside technical safeguards.
Employees who handle payments, approvals, sensitive data, or market-moving information, as well as managers who receive instructions via voice, video, or digital channels, should be prioritised due to higher exposure to impersonation attacks.
By preventing high-profile fraud incidents and misinformation spread, the training helps preserve client, investor, and regulator confidence, reducing long-term reputational and commercial damage.
The delivery is fully flexible. If you have an in-house LMS, we can provide the course as a SCORM-compliant package. If not, we offer a seamless SaaS-based hosting option for easy access and deployment.