- Engaging animated explainers simplify HIPAA Privacy, Security, and Breach Notification requirements
- Short, structured micro-modules enable quick understanding of PHI handling obligations
- Interactive scenarios reflect real healthcare situations
- Regulatory examples highlight common HIPAA violations and enforcement risks
- Embedded knowledge checks reinforce correct compliance decisions
- Final assessment with certification documents HIPAA awareness and due diligence
Learning Objectives
By the end of this course, learners will be able to:
- Identify the scope and applicability of HIPAA.
- Identify privacy requirements as per HIPAA Privacy Rule.
- Know security measures defined by HIPAA Security Rule.
- Tabulate Penalties, Breaches and Reporting guidelines.
Why HIPAA Covered & Non-Covered Entity Compliance Training?
Demonstrates proactive regulatory compliance and due diligence
The training directly aligns employees with the HIPAA Privacy Rule, Security Rule, and Breach Notification Rule, helping employers evidence that staff handling PHI understand when information may be used, disclosed, or must be protected - an expectation regulators consistently assess during audits and investigations.
Reduces the risk of costly civil and criminal penalties
The course clearly explains HIPAA’s tiered civil penalty structure (up to $1.5 million annually per violation category) and criminal liability for knowing misuse or unlawful disclosure of PHI. This equips employees to avoid behaviors that expose the organization to OCR (The Office for Civil Rights) enforcement and the U.S Department of Justice prosecution.
Addresses non-breach violations that still trigger enforcement
By highlighting that major penalties can arise even without a data breach, but for the violations of the HIPAA Regulations, the training corrects a common misconception and reinforces compliance obligations around improper disclosures, authorization failures, and inadequate safeguards that are frequent causes of enforcement action.
Strengthens workforce handling of PHI across all formats
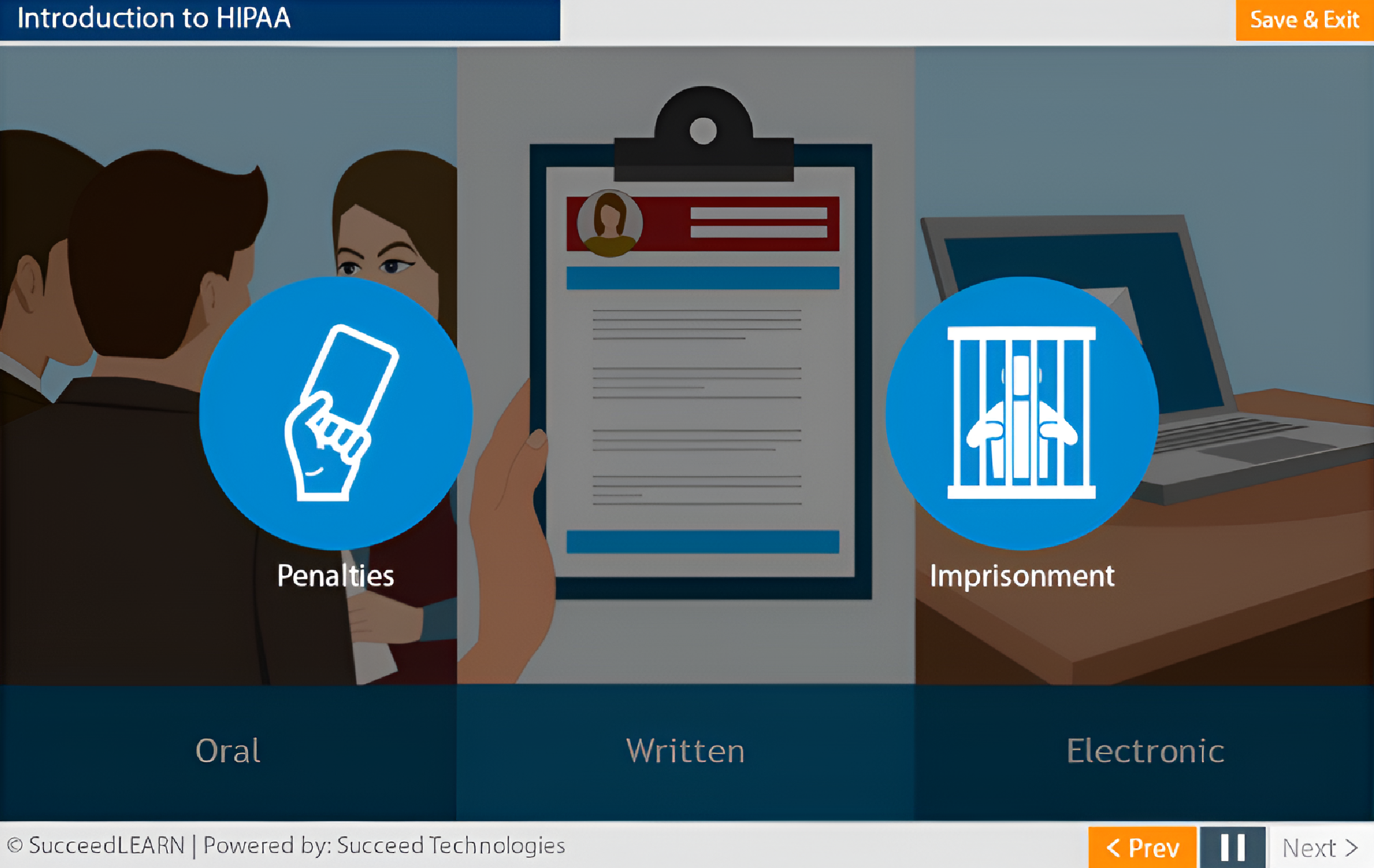
The course reinforces that HIPAA applies to oral, paper, and electronic PHI, ensuring employees understand that casual conversations, phone calls, emails, texts, and chats can all constitute violations if mishandled thereby reducing everyday operational risk.
Improves compliance with patient rights and response timelines
The training details statutory timelines for access requests (30 days), amendments (60 days), and accounting of disclosures (six years), reducing the risk of procedural non-compliance that can independently trigger regulatory scrutiny.
Strengthens cybersecurity posture through staff awareness
By addressing mobile device risks, email and texting controls, malware, unsecured Wi-Fi, and device loss, the course supports the employer’s administrative and physical safeguards under the Security Rule which are areas commonly cited in post-incident investigations.
Scenario-driven learning that mirrors real healthcare workflows
Interactive decision-making scenarios reflect actual clinical, administrative, and support-staff situations, enabling learners to apply HIPAA rules in practical contexts rather than relying on abstract legal explanations.
Laws & Regulations Addressed in HIPAA Covered & Non-Covered Entity Compliance Training
| Legislation / Concept | Relevance in the Course |
|---|---|
| Health Insurance Portability and Accountability Act (HIPAA) | The Health Insurance Portability and Accountability Act (HIPAA) is the foundational U.S. law governing how Protected Health Information (PHI) must be handled. In line with the law, the course equips healthcare professionals and business associates with practical knowledge to correctly use, disclose, secure, and report breaches of Protected Health Information (PHI), helping organizations meet HIPAA’s Privacy, Security, and Breach Notification requirements and reduce regulatory risk. |
Course Structure
Learning elements
Format & accessibility
Fully responsive interface across desktop, tablet, and mobile -complete with a learner dashboard, progress tracking, automated reminder prompts, and seamless integration with your existing LMS or HR systems.
Certificate
On successful completion and passing the assessment, learners can generate a completion certificate as proof of training (configurable per org).
Target Audience
The course is tailored for:
- Healthcare professionals handling patient information (clinical or non-clinical roles)
- Administrative and front-office staff with access to patient records or billing data
- IT, security, and EHR support teams managing electronic PHI (ePHI)
- Billing, coding, and claims processing personnel
- Compliance, privacy, and risk management teams
- Third-party vendors and service providers acting as Business Associates
Case Studies: Real Consequences of Non-Compliance
Under HIPAA, Covered Entities and Business Associates are mandatorily required to train their workforce members who have access to Protected Health Information (PHI) on HIPAA policies and procedures relevant to their roles.
Failure to train staff is a frequent root cause of HIPAA violations, enforcement actions, and penalties, even in the absence of a data breach.
Below are a few real cases where companies were penalised for not following compliance measures in line with HIPAA requirements:
- Anthem Inc. (2018) – USD 16 million settlement
Anthem paid the largest HIPAA settlement to date after a cyberattack exposed the ePHI of nearly 79 million individuals. OCR found failures in risk analysis, access controls, and ongoing workforce awareness thereby highlighting the consequences of weak HIPAA Security Rule compliance. - Memorial Healthcare System (2017) – USD 5.5 million settlement
Employees improperly accessed and disclosed PHI using shared login credentials. OCR specifically highlighted workforce access management failures, an issue directly addressed through role-based HIPAA training.
Course Outline
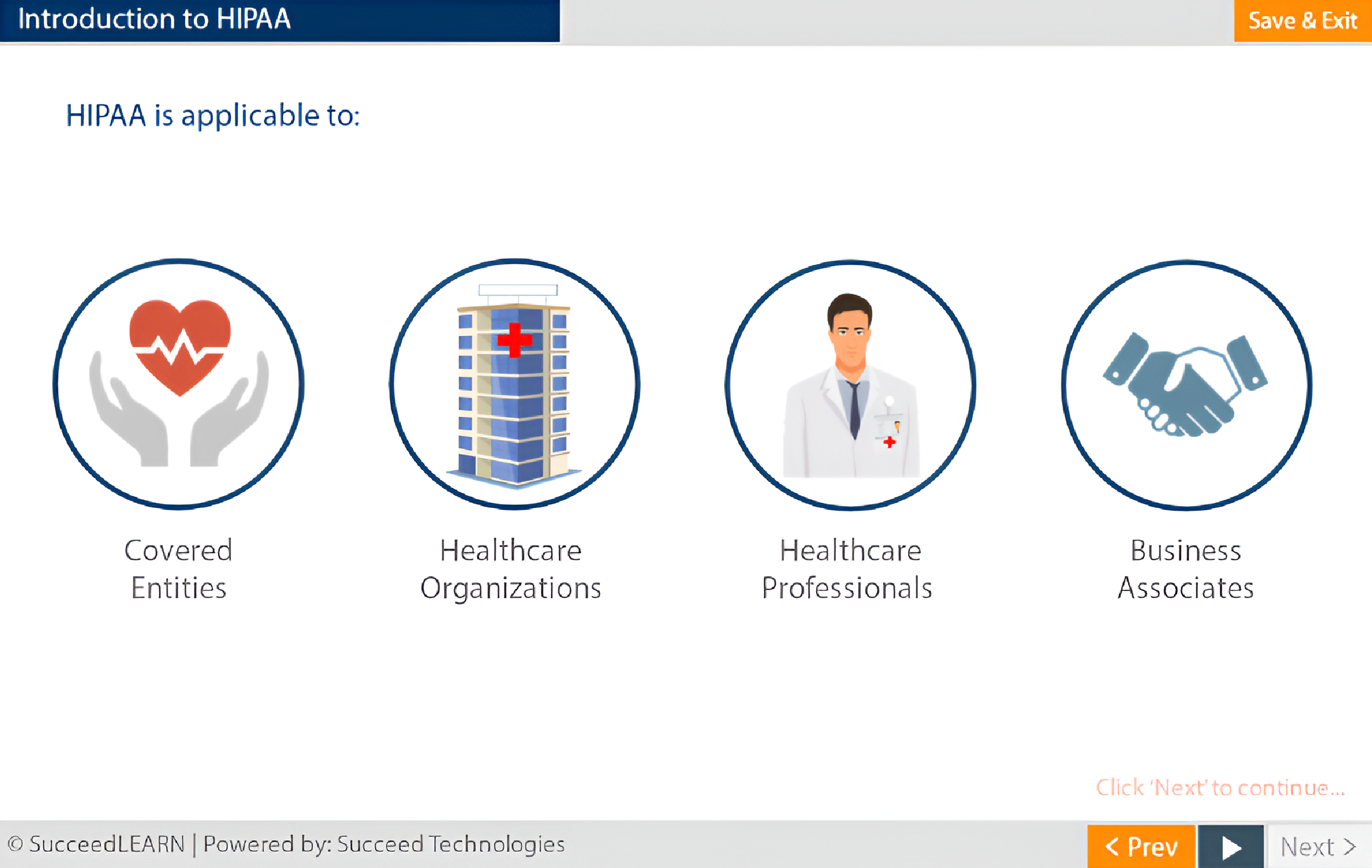
Introduction to HIPAA
Covered entities and their business associates:
- Health Plan,
- Health care clearinghouse,
- Health care provider and
- their Business associates.
HIPAA Privacy Rule
- Patients' Authorization
- Patient’s Rights
- Access to information
- Amending information
- Confidential communications
- Accounting of Disclosures
- Restrict information
- Notice of Privacy Practices
HIPAA Security Rule
- Administrative Safeguards
- Physical Safeguards
- Organizational Standards
- Policies and Procedures
- Cyber Attacks
- Cybersecurity measures
- Mobile Devices
- Email and Texting
Penalties, Breaches and Reporting
HIPAA Covered Entity vs HIPAA Non-covered Entity
| HIPAA Covered Entity | HIPAA Non-covered Entity |
|---|---|
| A HIPAA Covered Entity is an organization or individual directly regulated under HIPAA and legally responsible for protecting Protected Health Information (PHI). | A Non-Covered Entity is an organization or individual that does not fall under HIPAA’s definition of a Covered Entity and is not directly regulated by HIPAA. |
|
|
FAQs
HIPAA (Health Insurance Portability and Accountability Act of 1996) is a U.S. federal law that requires organizations handling health information to protect the privacy and security of patient data.
HIPAA training ensures employees understand how to correctly use, disclose, and safeguard Protected Health Information (PHI) across oral, paper, and electronic formats, reducing the risk of regulatory violations, penalties, and reputational damage, even in cases where no data breach occurs.
HIPAA establishes safeguards for how identifiable health information is accessed, used, and protected. This includes data such as medical histories, insurance and benefits information, and any health-related details that can be linked to an individual. In an HR context, this commonly arises during activities such as administering employee benefits, managing medical leave or accommodations, and handling workplace injury or wellness-related records. Although HIPAA obligations are formally imposed on covered entities, HR teams that support or operate within these structures are expected to follow HIPAA-aligned practices when handling employee health information.
HR teams often ask whether employee health data automatically falls under HIPAA. The answer depends on how and why the information is obtained.
- HIPAA applies when employee health information is created, received, or maintained as part of an employer-sponsored group health plan or related benefits administration activities.
- HIPAA does not apply to health details employees choose to share informally in the workplace, such as informing a supervisor about a medical absence. That said, this information may still be protected under employment laws, data protection regulations, or internal confidentiality policies.
No. HIPAA applies to all workforce members who may access PHI, including administrative staff, billing teams, IT personnel, and third-party Business Associates, as clearly illustrated through scenarios in the course.
The course covers the HIPAA Privacy Rule, Security Rule, and Breach Notification Rule, reinforcing high-risk areas such as minimum-necessary use, patient authorization, mobile device security, and breach reporting timeline that are areas frequently scrutinized by regulators.
It addresses common causes of enforcement actions, including improper verbal disclosures, misuse of email and chat tools, unencrypted devices, weak access controls, delayed breach reporting, and lack of workforce awareness, all highlighted through practical activities and assessments.
Employees are trained to identify what constitutes a breach, understand the difference between secured and unsecured PHI, and follow mandatory reporting timelines to individuals, HHS (U.S. Department of Health and Human Services), and the media where applicable thereby helping employers avoid secondary penalties for delayed notification.
Yes. The structured learning modules, scenario-based activities, knowledge checks, and final assessment provide documented evidence of workforce training, which regulators expect as a baseline compliance control during audits and investigations.
The training clearly explains Covered Entity and Business Associate responsibilities, emphasizing the need for proper controls, safeguards, and breach reporting that are critical for organizations operating within complex vendor and outsourcing ecosystems.
The delivery is fully flexible. If you have an in-house LMS, we can provide the course as a SCORM-compliant package. If not, we offer a seamless SaaS-based hosting option for easy access and deployment.